Guidelines to keep your devices safe from hackers
1. Keep Your Software Up to Date
One of the most important cyber security tips to mitigate ransomware is patching outdated software, both operating system and applications. This helps remove critical vulnerabilities that hackers use to access your devices. Here are a few quick tips to get you started:
- Turn on automatic system updates for your device.
- Make sure your desktop web browser uses automatic security updates.
- Keep your web browser plugins like Flash, Java, etc. updated.
2. Use Anti-Virus Protection & Firewall
Anti-virus (AV) protection software has been the most prevalent solution to fight malicious attacks. AV software blocks malware and other malicious viruses from entering your device and compromising your data. Use anti-virus software from trusted vendors and only run one AV tool on your device.
Using a firewall is also important when defending your data against malicious attacks. A firewall helps screen out hackers, viruses, and other malicious activity that occur over the Internet and determines what traffic is allowed to enter your device. Windows and Mac OS X come with their respective firewalls, aptly named Windows Firewall and Mac Firewall. Your router should also have a firewall built in to prevent attacks on your network.
3. Use Strong Passwords & Use a Password Management Tool
You have probably heard that strong passwords are critical to online security. The truth is passwords are important in keeping hackers out of your data! According to the National Institute of Standards and Technology’s (NIST) 2017 new password policy framework, you should consider:
- Dropping the crazy, complex mixture of upper-case letters, symbols, and numbers. Instead, opt for something more user-friendly but with at least eight characters and a maximum length of 64 characters.
- Not using the same password twice.
- Selecting a password that contains at least one lowercase letter, one uppercase letter, one number, and four symbols but not the following &%#@_.
- Choosing something that is easy to remember and never leaving a password hint out in the open or making it publicly available for hackers to see
- Resetting your password when you forget it. But change it once per year as a general refresh.
4. Use Two-Factor or Multi-Factor Authentication
Two-factor or multi-factor authentication is a service that adds additional layers of security to the standard password method of online identification. Without two-factor authentication, you would normally enter a username and password. But, with two-factor, you would be prompted to enter one additional authentication method such as a Personal Identification Code, another password or even a fingerprint. With multi-factor authentication, you would be prompted to enter more than two additional authentication methods after entering your username and password.

According to NIST, an SMS delivery should not be used during two-factor authentication because malware can be used to attack mobile phone networks and can compromise data during the process.
5. Learn about Phishing Scams – be very suspicious of emails, phone calls, and flyers
In a phishing scheme attempt, the attacker poses as someone or something the sender is not to trick the recipient into divulging credentials, clicking a malicious link, or opening an attachment that infects the user’s system with malware, a trojan virus, or a zero-day vulnerability exploit. This often leads to a ransomware attack. In fact, 90% of ransomware attacks originate from phishing attempts.
A few important cyber security tips to remember about phishing schemes include:
- Bottom line – Do not open email from people you do not know
- Know which links are safe and which are not – hover over a link to discover where it directs to
- Be suspicious of the emails sent to you in general – look and see where it came from and if there are grammatical errors
- Malicious links can come from friends who have been infected too. So, be extra careful!
6. Protect Your Sensitive Personal Identifiable Information (PII)
Personal Identifiable Information (PII) is any information that can be used by a cybercriminal to identify or locate an individual. PII includes information such as name, address, phone numbers, data of birth, Social Security Number, IP address, location details, or any other physical or digital identity data.
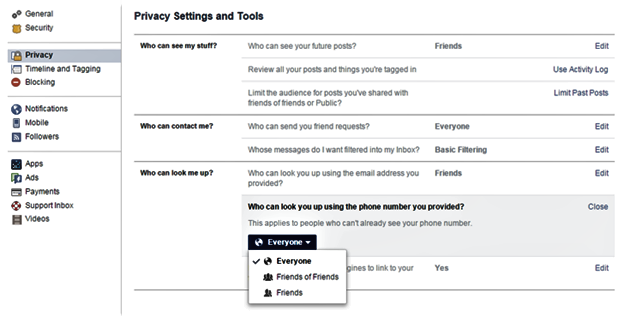
In the new “always-on” world of social media, you should be very cautious about the information you include online. It is recommended that you only show the very minimum about yourself on social media. Consider reviewing your privacy settings across all your social media accounts, particularly Facebook. Adding your home address, birthdate, or any other PII information will dramatically increase your risk of a security breach. Hackers use this information to their advantage!
Facebook Privacy Settings
7. Use Your Mobile Devices Securely
According to McAfee Labs, your mobile device is now a target to more than 1.5 million new incidents of mobile malware. Here are some quick tips for mobile device security:
- Create a difficult mobile passcode – not your birthdate or bank PIN
- Install apps from trusted sources
- Keep your device updated – hackers use vulnerabilities in unpatched older operating systems
- Avoid sending PII or sensitive information over text message or email
- Leverage Find my iPhone or the Android Device Manager to prevent loss or theft
- Perform regular mobile backups using iCloud or Enabling Backup & Sync from Android
Practice these safeguards and you’re taking smart steps in preventing your devices from being hacked, saving yourself from potential drastic consequences.
